Blocking ads with Pi-hole
2024-08-20
Per wiki, Pi-hole is a Linux network-level advertisement and Internet tracker blocking application which acts as a DNS sinkhole and optionally a DHCP server, intended for use on a private network. In other words, it can effectively block unwanted ads, telemetry, logging, or basically any kind of traffic that you can define at the network level.
Pi-hole set up
- Install Pi-hole on your local server.
- Update router configuration to use Pi-hole as DHCP and DNS servers.
- Update the ads servers. I don't recall where I got mine but this is my list for reference. You can also find plenty from reputable sources online.
https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts
https://raw.githubusercontent.com/PolishFiltersTeam/KADhosts/master/KADhosts.txt
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/add.Spam/hosts
https://v.firebog.net/hosts/static/w3kbl.txt
https://adaway.org/hosts.txt
https://v.firebog.net/hosts/AdguardDNS.txt
https://v.firebog.net/hosts/Admiral.txt
https://raw.githubusercontent.com/anudeepND/blacklist/master/adservers.txt
https://s3.amazonaws.com/lists.disconnect.me/simple_ad.txt
https://v.firebog.net/hosts/Easylist.txt
https://pgl.yoyo.org/adservers/serverlist.php?hostformat=hosts&showintro=0&mimetype=plaintext
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/UncheckyAds/hosts
https://raw.githubusercontent.com/bigdargon/hostsVN/master/hosts
https://v.firebog.net/hosts/Easyprivacy.txt
https://v.firebog.net/hosts/Prigent-Ads.txt
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/add.2o7Net/hosts
https://raw.githubusercontent.com/crazy-max/WindowsSpyBlocker/master/data/hosts/spy.txt
https://hostfiles.frogeye.fr/firstparty-trackers-hosts.txt
https://raw.githubusercontent.com/DandelionSprout/adfilt/master/Alternate%20versions%20Anti-Malware%20List/AntiMalwareHosts.txt
https://osint.digitalside.it/Threat-Intel/lists/latestdomains.txt
https://s3.amazonaws.com/lists.disconnect.me/simple_malvertising.txt
https://v.firebog.net/hosts/Prigent-Crypto.txt
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/add.Risk/hosts
https://bitbucket.org/ethanr/dns-blacklists/raw/8575c9f96e5b4a1308f2f12394abd86d0927a4a0/bad_lists/Mandiant_APT1_Report_Appendix_D.txt
https://phishing.army/download/phishing_army_blocklist_extended.txt
https://gitlab.com/quidsup/notrack-blocklists/raw/master/notrack-malware.txt
https://v.firebog.net/hosts/RPiList-Malware.txt
https://v.firebog.net/hosts/RPiList-Phishing.txt
https://raw.githubusercontent.com/Spam404/lists/master/main-blacklist.txt
https://raw.githubusercontent.com/AssoEchap/stalkerware-indicators/master/generated/hosts
https://urlhaus.abuse.ch/downloads/hostfile/
https://github.com/ewpratten/youtube_ad_blocklist/blob/master/blocklist.txt
Results & final thoughts
This is what my Pi-hole dashboard looks like.
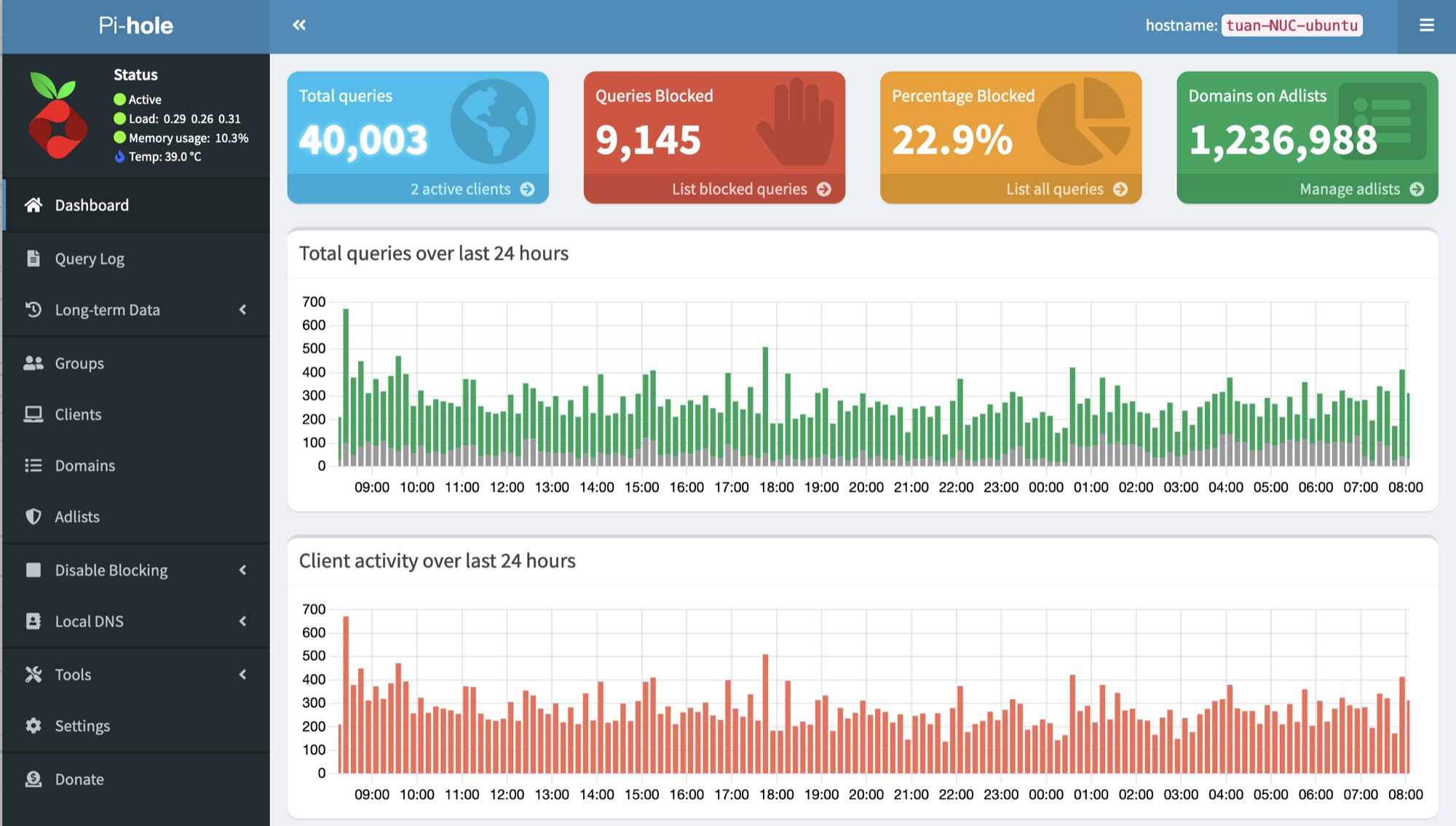
- The blocking happens at the network level, i.e. Pi-hole server and router. Any other device on your local network will get protection by default.
- 23% of the queries are blocked. This is a staggering amount of traffic but note that
- it probably includes retries (due to blocked traffic) which skews the metric a bit,
- it's the request volume, not the bandwidth.
- It's possible to define blocking rules per time and clients (i.e., certain devices on the network). For example I can allow my TV to connect to Netflix but block all other devices from doing so.
- Pi-hole runs as a server so you can remotely control that (with additional set up). For example, you're on a trip and find suspicious activities on your PC (this is another story for another day). Then you can remotely block all online banking traffic on your home network.
- Given a custom DNS server, you can do all kind of testings or set up a honeypot.